Keywords:-IDS, Intrusion Detection System, What are the types of IDS, IDS methodologies, IDS in detail
#1. Introduction to IDS:
Intruder is just a person who can be outsider(masquerade) or insider(misfeasor). An intruder has a criminal intention to get unauthorized access to the system in order to modify or delete the data. Here ofcourse outsider does not have access to the system hence he just finds the opportunity where there is loss of integrity, confidentiality. Insider tries to misuse the given privileges. In order to prevent such kind of malicious activities we use a system named as Intrusion Detection System.
An IDS is a system that continuously monitors the network and detects/ identifies the malicious activities in order to prevent the occurrence of malicious activities. How ever if any malicious activity is detected the system admin is notified regarding it with an alarm.
#2. Types of IDS
1. NIDS
- NIDS stands for Network Based Intrusion Detection System.
- As the name specifies its a Network based IDS.
- NIDS just checks the current attack with the known attack stored in the system.
- NIDS monitors, captures, analyzes the traffic in order to detect any kind of harmful activity.
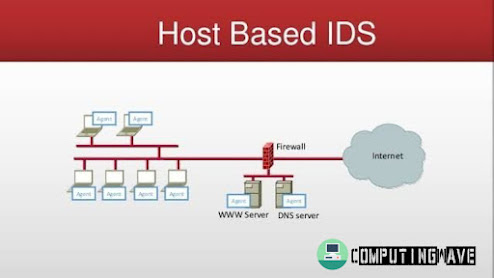
2. HIDS
- HIDS stands for Host Based Intrusion Detection System.
- As the name specifies the intrusion detection system is based on host.
- HIDS is installed on individual host or device.
- 'HIDS monitors the data packets from the devices only and will alert the admin only if any suspicious activity is found
#3. IDS methodologies
IDS has two methodologies they are as follows:
1. Signature Based IDS
- It is the best solution for known threats.
- It operates by preprogrammed list of known threats.
- Signature based IDS monitors the packets that traverse through the particular network.
- It compares the data packets with the packets in database or known IOC(Indicator of Compromise)
2. Anomaly Based IDS
- Anomaly based IDS is the best solution for unknown attacks.
- It uses machine learning to train the detection system to recognize a normalized baseline.
- Base line shows how the system normally behaves and then all network activity is compared to the baseline.
- Anomaly based IDS simply identifies any out of the ordinary behavior to trigger alerts.
#4. Comparison of IDS with firewalls.
No doubt, IDS and firewall both are dedicated for the security of the network but however they are different from each other.
a. Firewall decides to allow or not allow based on set of rules, while IDS detects the suspicious activity and notifies.
b. Firewall restricts the acccess to the network to prevent attack, while an IDS describes a suspected intrusion once it has happened and then sends the alarm.
#5. Application Of IDS
- It is a tool used to monitor a network to prevent intrusion.
- After a suspicious activity is found the user is notified with the help of alarm.
- IDS contributes for the security of the system/network by restricting unauthorized access.
- IDS is a much needed tool to keep our data safe and far from malicious activities