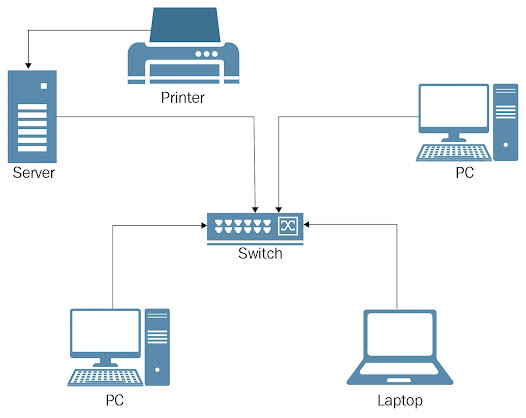
2. LAN
a. LAN stands for Local Area Network.
b. Its used in Offices, educational institutes etc.
c. Range: <150 meter
d. Easy to maintain
3. MAN
a. MAN stands for Metropolitan Area Network.
b. It is a combination of various LAN networks.
c. Range: <50 KM
d. It is used within city.
d. Difficult to maintain.
4. WAN
a. WAN stands for Wide Area Network.
b. WAN is a combination of many LAN and WAN networks.
c. Range is not determined.
d. It is used for all countries or all around the world.
d. Difficult to maintain.
Network Devices:
1. Hub:
a. Network device to connect multiple computers in a network.
b. All information sent to hub is sent to all devices in the network(Broadcasting).
c. Less expensive, less intelligent, and less complicated.
d. Mainly used in LAN.
e. Transmission is half duplex.
Advantages:
1. Hub can broadcast the message.
2. It is less expensive and anyone can use it.
3. Easy Installation.
4. Robust.
Disadvantages:
1. If the hub fails entire network will be failed.
2. We can't send private/personal data through hub.
3. Hub does not provide any security.
4. Hub cannot support full duplex transmission mode.
2. Switch:
1. Switch is a network device that connects multiple computers together in a network.
2. It is used to send private message.
3. There is no wastage of data.
4. It can identify which device is connected with which port by using MAC address, that's why it delivers message on a particular machine.
5. It is more intelligent than hub, because it notes down the address of source and destination machine, according to it data is delivered.
Advantages
1. It is used to unicast the message.
2. It provides more security than hub.
3. Switch supports full duplex transmission mode.
4. It sends the data packets based on the MAC address.
5. If a node fails, there will be no effect in the entire network.
Disadvantages
1. If a switch fails than a entire network will be failed.
2. It is more expensive.
3. Difficult to set up.
3. Router
1. Router is a network device which works as a traffic controller.
2. It's main work is to find a congestion free path, through which the packet will travel.
3. Router receives data packets from the sender, analyzes it and forwards them to receiver.
4. It uses both LAN and WAN.
Advantages:
1. It provides connection between two distinct types of network.
2. Transmission rate is very high.
3. It internally uses some algorithm to findout congestion free path.
4. It works with both wireless and wired data.
Disadvantages:
1. Router is more expensive as compared to other network devices.
2. Routers are more complex to maintain.
3. Security issues.
4. It works only with routable protocol.
4. Repeater.
1. Repeater is a network device through which we can boast up the weak signal.
2. When the signal travels some distance the intensity of the signal becomes low.
3. In order to regenerate weak signal we should use repeater device.
4. It is used in wired and wireless both type of devices.
5. Some decades ago it was used in cable TV.
Advantages
1. It is used to regenerate the weak signal.
2. It is cheaper than other network devices.
3. It has the ability to extend the length of the network signal.
4. It maintains the signal performance.
Disadvantages:
1. It requires many repeaters after some distance.
2. They are unable to connect different type of network.
3. They can't reduce network traffic.
4. Bridge
1. Bridge is a network device that is used to separate LAN intro number of sections.
2. It works on physical and data link layer of OSI.
Advantages:
1. By using bridge, we can extend our network.
2. It broadcasts the data to each node.
3. Collisions can be reduced.
4. It is more intelligent.
Disadvantages:
1. It doesn't establish connection between two diffferent network.
2. Once it broadcasts the message then it is unable to stop the messages.
3. It is more expensive.
4. The transmission rate is slower.
5. Gateway:
1. A gateway is a hardware device that is used to connect two dissimilar type of network.
2. It allows us to send and recieve data through internet even when it is LAN.
3. It operates on all 7 layers of OSI model.
Advantages:
1. It can connect two network that has different protocol.
2. Operates on all 7 layers of OSI model.
3. We cannot access internet without a gateway.
4. It provides some security.
Disadvantages:
1. It is more expensive.
2. Data transmission rate is slower.
3. Difficult to maintain as well as it is very complex.
4. It is very intelligent.
6. NIC:
1. NIC stands for Network Interface Card.
2. It is a hardware device without which we cannot connect to network/ internet.
3. It has two types; Internal Network Card and External Network Card.
a. Internal Network Card:
1. In this card the motherboard has a slot for the network card where it can be inserted.
2. It requires a network cable to provide network access.
b. External Network Card:
1. In desktops and laptops that does not have an internal NIC, external can be used.
2. It has two types; Wireless and wired(USB Cabl3).
Advantages:
1. It allows to connect your device with other device.
2. It has wired and wireless facility for enabling connectivity.
3. Allows to connect using IP Address and LAN.
Disadvantages:
1. Data is not secure.
2. Wireless connection is not portable.
3. Configuration of setup is difficult.
7. Modem:
1. Modem stands for modulator and demodulator.
2. It is a network device that is placed between computer system and telephone lines.
3. It has two parts; modulator and demodulator.
4. Modulator: It converts digital signal to analog signal.
5. Demodulator: It converts analog signal to digital signal.
Advantages:
1. The data sent in a particular form will reach to reciever in the same form.
2. It can be used to send data at a large distance.
3. Data transfer speed is fast.
Disadvantages:
1. Data cannot be sent without wire.
2. Data transfer becomes slow depending on the distance.
TOPOLOGY:
1. Topology is a physical arrangement of the computer system , which is connected to each other via communication medium.
2. In computer network it has 6 types; Bus, Ring, Star, Mesh, Tree, Hybrid.
1. BUS TOPOLOGY.
In bus topology cable are connected as a single communication channel and all the devices are connected to the cable.
Advantages:
1. Easy to add/ remove nodes in a network.
2. Requires only one cable.
3. It is less expensive.
4. It broadcasts the message to each device which are connected through the cable.
5. It is easy to miantain.
6. In case of any computer failure, there will be no effect on the other devices.
Disadvantages:
1. If the cable fails entire network will be failed.
2. The messages are broadcasted so we cannot send private message.
3. It takes more time to send private message from one place to another.
4. Length of wire is limited.
5. Data is transmitted in only one direction.
2. RING TOPOLOGY
1. It is called ring topology because it forms a shape like ring.
2. In this topology each node is strongly connected with it's adjacent node.
Advantages:
1. It has a strong network.
2. Each and every node can share data with another node connected in a ring topology.
3. Transmission rate of dats is very fast.
4. The data sent through ring topology will be broadcasted.
Disadvantages:
1. It is very difficult to add some new devices.
2. If we want to send data from a source to destination machine, then data will be unnecessarily passed to all nodes.
3. Single point of failure , that means even if a node goes down all network goes down.
4. We can't send message properly.
3. STAR TOPLOGY
1. In star topology all the device are connected with a central device called as HUB.
2. Sharing of data is possible only through hub.
Advantages:
1. It broadcasts the message.
2. It is less expensive due to less cable.
3. Easy to connect new nodes without affecting rest of the network.
4. If a node fails, it won't affect the entire network.
Disadvantages:
1. In a star topology, we must requirea network device like hub, switch. etc.
2. If two nodes want to share the data, sharing is possible only through hub.
3. If a hub fails entire network will be failed.
4. We can't send private data.
4. MESH TOPOLOGY.
1. In this topology, each and every network is connected with each other.
2. We can directly send the data to the destination machine without going to intermediate machine.
Advantages:
1. It is a very good topology to send private data.
2. All nodes are connected together, it provides point to point connection.
3. Unlike ring topology, if a particular machine fails then entire network will not be failed.
4. Multiple devices can send and recieve data simulataneously.
Disadvantages:
1. It is very difficult to add new node because each and every node is connected with one another.
2.If a particular machine is not working we can't send and recieve data from the failure machine.
5. TREE TOPOLOGY
1. All nodes are connected like branches of tree in tree topology.
2. We can also say bus and star topology together form a tree topology.
Advantages:
1. Easy to expand by adding more branches or levels, making it suitable
for growing networks.
2. If a branch fails, only the devices on that branch are affected, minimizing
network disruptions.
3. The central hub allows for centralized network management and
monitoring.
4. Each device has a dedicated connection, reducing collisions and
improving data transmission.
Disadvantages:
1. The central hub is a critical point, and if it fails, the entire
network can be disrupted.
2. Requires more cabling than some other topologies, which can be costly
and challenging to manage.
3. High traffic on the central hub can lead to performance issues and
slower data transfer.
4. Network maintenance and troubleshooting can be more complex due to
the hierarchical structure.
6. HYBRID TOPOLOGY.
1. Hybrid topology is a combination of various other topologies.
Advantage:
[As per the combination of the topologies the advantages can be listed, consider taking 2 topologies for writing points]
Disadvantages:
[As per the combination of the topologies the disadvantages can be listed, consider taking 2 topologies for writing points]
Protocols:
Protocols are a set of rules used in digital communication to connect network devices and exchange information between sender and receiver.
Types of protocols:
1. TCP/IP:
1. TCP stands for Transmission Control Protocol, and IP stands for Internet Protocol.
2. TCP is used to transfer data over internet and IP address is used for addressing through which data reaches final destination.
2. HTTP: HTTP stands for Hyper Text Transfer Protocol which is used in the address bar of the web browser before WWW, it brings the website in front of us whenever we search anything.
3. FTP: FTP stands for File Transfer Protocol, which is used to send file from sender to client machine and vice versa.
4. SMTP: Simple Mail Transfer Protocol is used along with POP and IMAP protocol to send and receive emails over the internet.
5. POP: Post Office Protocol is a mail box which is actually a mesage access protocol through which a user can fetch email from the server , and helps the SMTP protocol for end to end communication.
6. IMAP: Internet Mail Access Protocol is improved version of POP , but the main advantage is that we can retrieve our deleted email from the server.
7. PPP: Point To Point Protocol is used to transfer data between two directly connected devices.
8. UDP: User Datagram Protocol is an unreliable and connectionless protocol to transfer data in a short distance.
Design Issues for network layer:
Design issues in the network layer, which is responsible for routing data across networks, can be summarized in seven key points:
1. Routing Algorithms: Choosing the right routing algorithms to efficiently forward data packets in a network, considering factors like speed, reliability, and scalability.
2. Addressing: Defining how devices are addressed and identified within the network, such as IP addressing in the case of the Internet.
3. Packet Forwarding: Establishing mechanisms for forwarding data packets from source to destination, including hop-by-hop routing and header processing.
4. Scalability: Ensuring that the network can grow and handle increasing traffic without significant performance degradation.
5. Quality of Service (QoS): Implementing QoS mechanisms to prioritize and manage traffic to meet different application requirements (e.g., voice, video, data).
6. Security: Integrating security measures to protect against unauthorized access, data breaches, and denial-of-service attacks.
7. Interoperability: Ensuring that different network technologies and protocols can work together seamlessly, promoting compatibility and connectivity across diverse networks.
OSI Model:
Imagine you're sending a letter to a friend who lives far away, and you want to make sure the message gets to them correctly. The OSI Model is like a guide that helps computers and devices communicate with each other, just like your letter needs to go through different steps to reach your friend.
The OSI Model has 7 layers, and each layer has a specific job:
Physical Layer (Layer 1): This is like the envelope and the paper you write your letter on. It deals with sending raw bits of data over physical cables or wireless connections.
Data Link Layer (Layer 2): This is like the address on the envelope. It makes sure data gets from one device to the next without any mistakes. It also handles things like managing traffic on the connection.
Network Layer (Layer 3): This is like the postal system that figures out the best route for your letter to take to reach your friend's city. It deals with addressing and routing data packets between different networks.
Transport Layer (Layer 4): This is like making sure your letter is split into manageable parts and put back together correctly on the other end. It also checks if any parts are missing and asks for them again.
Session Layer (Layer 5): This is like keeping track of the conversation you're having with your friend throughout multiple letters. It manages the communication sessions and makes sure everything is in order.
Presentation Layer (Layer 6): This is like translating your letter into a language your friend understands, or maybe even encrypting it so only your friend can read it. It takes care of data translation and encryption.
Application Layer (Layer 7): This is like the content of your letter - the actual message you want to share with your friend. It's where software applications and programs that need network services communicate.
So, just like sending a letter involves different steps to make sure it gets to your friend correctly, the OSI Model breaks down how computers and devices work together to send and receive data across networks. Each layer has its own job, and they all work together to ensure smooth communication.
TCP/IP Model:
Let's simplify understanding the TCP/IP model:
Think of the TCP/IP model like sending a letter through the postal service.
1. Application Layer (Sender's Letter): This is where you write your letter or message. You decide what you want to say and put it in an envelope. In computer terms, this layer deals with software applications like web browsers, email programs, or games.
2. Transport Layer (Sender's Sending Method): Now that you have your letter, you decide how to send it, like choosing between regular mail, express delivery, or registered mail. In computers, this layer handles how your data should be sent - fast but maybe less reliable (like pizza delivery) or carefully with tracking (like registered mail). It's also in charge of making sure all parts of your letter arrive correctly.
3. Internet Layer (Postal Addresses): Just like you need the recipient's address to send a letter, the Internet Layer uses IP addresses to find where to send your data. It's like the postal service figuring out which town and street your letter needs to go to.
4. Link Layer (Packaging and Pickup): Before your letter goes out, it's put in an envelope, maybe a box, and labeled with the destination address. In computers, this layer deals with getting your data ready for transport, like putting it in packets (small parts) and handling the physical connection, such as Wi-Fi or Ethernet cables.
5. Physical Layer (Actual Delivery): Finally, the letter or package physically moves from your place to the recipient's place through roads, trucks, or planes. In computers, this layer manages the actual hardware, like the wires, signals, and devices that physically carry your data from one place to another.
So, just like sending a letter, the TCP/IP model breaks down how your data goes from your computer (sender) to another computer (recipient) by preparing it, finding the address, deciding how to send it, and physically moving it. This way, computers all over the world can talk to each other and share information.
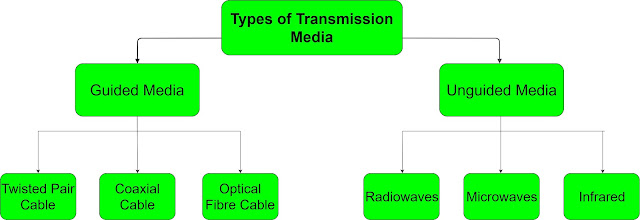
Types of Transmission medium
A. Wired/Guided media
1. Twisted cable
2. Coaxial cable
3. Fiber optic
B. Wireless/ unguided media
1. Radio waves
2. Microwaves
3. Infrared waves
A. Guided media - Are those which provide a connection from one device to another, which include twisted pair cable, coaxial cable and fiber optic.
1. Twisted Pair Cable
-Used in LAN, telephone line
- Consists of two conductors (copper), eachwith its own plastic insulation twisted together.
- It has shielded and unshielded pair of cable.
2. Coaxial cable
-Used in TV.
-It has a central core of solid wire enclosed in an insulating sheath which in turn , encased in an outer conductor of metal foil , braided or a combination of two.
-Made of glass/plastic and transmit signal in the form of light, using the principle of internal reflection , a glass / plastic core is surrounded by a cladding of less dense glass plastic.
-Backbone network cost effective can go up to 1600 Gbps (higher bandwidth, less signal attenuation, ne noise problem, no corrosion, light weight, greater immunity to tapping)
B. Unguided media
1.Radio waves.
2. Microwaves
3. Infrared waves
-In unguided media air is the media through which the electromagnetic energy can flow easily.
- It transmits the electromagnetic waves without using physical media
1. Radio waves: It transmits waves in all direction if free space.
2. It has omnidirectional waves
3. Range → 3Khz to 1 Khz
4. In case the sending and receiving antenna are not aligned such that the wave received by sending antenna can be received by an receiving antenna.
Applications:
1. Multicasting: Sending data to many users
2. FM radio, Television, cordless phones etc.
2. Microwave: Types
1. Terrestrial microwaves
2. Satellite microwave communication
1. Terrestrial Microwave Transmission: - Transmits the focused bean of a radio signal from one ground based microwave transmission antenna.
- Frequency : 1GHZ to 100 GHZ
- It is unidirectional
2. Satellite microwave Communication:
-A satellite is a physical object that revolves around the earth at a known height
- -A satellite communication is more reliable nowadays as it offers more flexibility than cable & Fiber optics system -We can communicate with the globe by using satellite communication.
3. Infrared:
-An infrared transmission to wireless technology used for communication over short ranges ---Frequency → 300GHz to 400GHz
- It is used for short range communication such as data transfer between two cell phones, TV remote operations, data transfer between a computer and a cell phone that are in the same closed area.
Characteristics
1. It has high bandwidth and hence the data rate will be very high.
2. Infrared waves cannot penetrate the walls, therefore infrared communication in one room cannot be interrupted by nearby rooms
3. Provides better security with minimum interference
4. It is unreliable outside the building because the sun rays will interfere with the infrared waves
Network Architecture
1. Network architecture means network layout that tells us how computers are arranged and how tasks are allocated to computer.
Types
1. Peer to Peer architecture
2. Client Server architecture
1. Peer to Peer architecture:
1. It is also known as point to point network which all the computers are linked directly together with equal privileges and responsibilities for sharing data.
2. There no server in it.
Advantages
1. It is cheaper, because it has no server.
2. If one computer will stop working, it will have no effect on the other computer.
3. It's setup and maintenance is easy.
- Disadvantage
1. Security issues ( no server).
2. We cannot backup the data because there is no server in it.
2. Client Server Architecture:
- It is also known as request response architecture
- In this architecture client makes a request to the servers and server will fulfill the response.
Advantages:
1. It has centralized system from which data can be easily backed up.
2. Security is better.
3. Entire system is maintained by the server.
4. It also increases speed of response sharing.
Disadvantages:
1. In case of server failure entire network will be failed
2. Server maintenance will be high
3. Hybrid: It is a combination of both architecture peer to peer & client server
Line Coding
Line coding is like translating a secret message into a special language, and then back into the original message.
1. Translation: Imagine you have a message made of zeros (0s) and ones (1s). Line coding turns these 0s and 1s into a special kind of signal.
2. Sending: This special signal is sent through wires or fibers to someone else.
3. Translation Back: The person on the other end receives this special signal and turns it back into the original message, full of 0s and 1s.
So, line coding is like speaking a secret code in binary (0s and 1s) that can travel through wires and then get decoded to reveal the original message. It helps computers talk to each other over distances
Let's break down the classification of line coding (unipolar, bipolar, and polar) in a simple way:
1. Unipolar: Unipolar line coding is like a light switch. Imagine you have a room with one light bulb. When the light is off, it represents the number "0." When you turn it on, it represents "1." There's only one way to represent data - with the light on or off. It's simple, but it can have a problem with always being on or off, like a constant bright light or complete darkness.
2. Bipolar: Bipolar line coding is like a seesaw. Think of a playground seesaw with two sides. When one side is up, it represents "1," and when the other side is up, it represents "0." It goes back and forth, so you get a balance between "1"s and "0"s. This is good because it avoids a constant up or down situation.
3. Polar: Polar line coding is like using two different colors of crayons. Imagine you're drawing a picture, and you have two crayons - one red and one blue. You can use red to mean "1" and blue to mean "0." This gives you a way to show your drawing in two different colors, so you have more flexibility in your message.
In short, unipolar is like using one light, bipolar is like a seesaw, and polar is like using different crayons to express your data. Each method has its own advantages and disadvantages in sending and receiving digital information.
Manchester and Differential Manchester
Manchester Encoding:
- Manchester encoding is a method of line coding used in computer networking and communication.
- Imagine a timeline where you want to send digital data, which consists of 0s and 1s.
- In Manchester encoding, each bit period is divided into two halves.
- The transition from a low voltage level to a high voltage level (or vice versa) in the middle of the bit period represents a "1."
- The absence of a transition in the middle of the bit period represents a "0."
- This encoding scheme ensures there is always a transition in the middle of each bit, making it self-clocking, which helps in synchronization between sender and receiver.
- Manchester encoding is commonly used in Ethernet and is known for its reliability in data transmission.
Differential Manchester Encoding:
- Differential Manchester encoding is another line coding scheme used in computer networking.
- Like Manchester encoding, it also divides each bit period into two halves.
- However, in Differential Manchester encoding, the presence or absence of a transition at the beginning of the bit period represents the value.
- A transition at the start indicates a "0," and no transition at the start represents a "1."
- Unlike regular Manchester encoding, Differential Manchester has transitions at the start of each bit, not the middle.
- This encoding scheme is also self-clocking and aids in synchronization.
- It is commonly used in Token Ring networks.
FHSS and DHSS:
FHSS (Frequency-Hopping Spread Spectrum):
- FHSS is like a secret code that changes its frequency quickly, like a radio station that keeps switching between different channels.
- Imagine you want to send a message, but you don't want others to easily intercept it.
- FHSS works by taking your message and quickly hopping or jumping between different radio frequencies, like changing the radio station every second.
- The receiver knows the sequence of jumps, so it can hop along with the sender and catch the message.
- It's like speaking in a secret language that only you and your friend understand because you both know the order of frequencies to listen to.
- FHSS is used in things like Wi-Fi and Bluetooth to make sure your data is transmitted securely.
DSSS (Direct-Sequence Spread Spectrum):
- DSSS is like adding extra noise to your message to protect it.
- Imagine you're sending a message, and you mix it with random gibberish before sending it.
- At the other end, the receiver knows the gibberish pattern and can filter it out to get the original message.
- It's a bit like hiding a precious gem in a pile of shiny rocks, and only someone with the right filter can find the gem.
- DSSS spreads the data out over a wider frequency band, making it more resistant to interference and eavesdropping.
- It's used in some wireless communication systems to keep your data safe from prying ears.